
- Read 125Khz tags
- Emulate 125Khz tags
- Save tag data in memory
- Bruteforce 125Khz readers
- Manual mode
- Write to magic tags
Prelude :
Recently the building where I live got an upgrade with an access controller, a bunch of tags have been distributed to the residents with $$$ to pay for extra tags, the reason I needed to start my journey into understanding and bending this technology for educational purposes (of course)
theory
The Journey :

Recon :
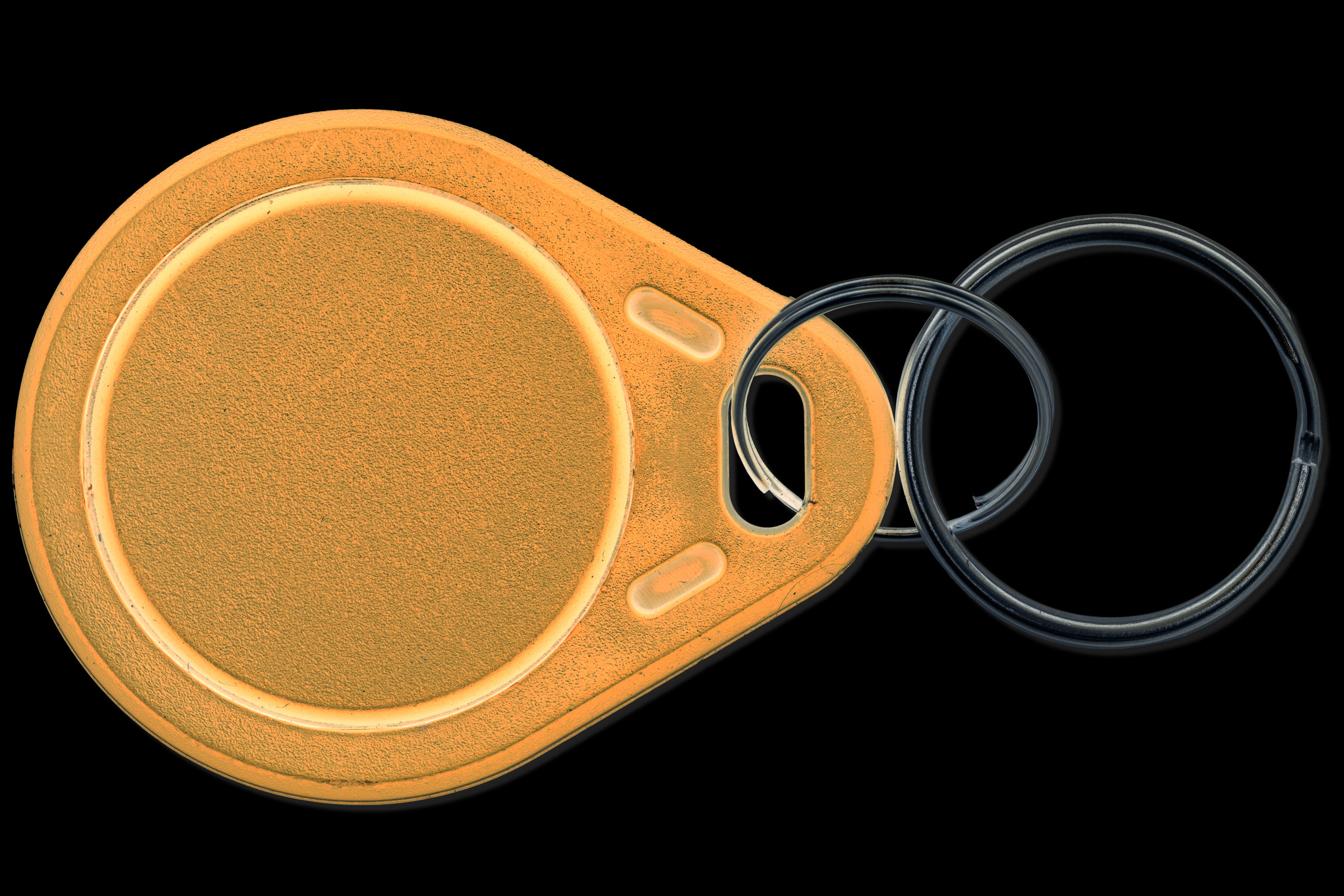
First things first, the access token was looking like any NFC Tag with a keychain, I remember smartphones are able to read those, my first smartphone (a trusty and waterproof Xperia V back in the days) was promoted with the NFC feature, an quick and interesting way to share links and texts between phones, so popped my worthy Nethunter (Oneplus5T unofficial build) and tried reading it, Nothing.
Gave it another try with NFC Tool app and the only thing I got was me rubbing the tag against my phone flattering my ADHD ..
After few researches, appeared that the most common NFC tags comes in two flavors :
13.56Mhz NFC
- High Frequency
- Writable
- 2 ways
- Can store to 4Kb of data
- Can be encrypted
- Smartphone compatible

125Khz NFC
- Low Frequency
- Not Writable (*)
- 1 way
- 64 bits memory
- cannot be encrypted
- too low frequency for smartphone
Most common tags, Abusively called Mifare tags, as mifare is the chip inside responsible of the memory and frequency resonance, they’re not all mifare, hundreds of chips are available today and everyone is going with his sauce on the hard formatting and encryption, Mifare, Ntag, Slix, ST25 …etc..
a cheap alternative, low frequency based on TK4100 and EM4100 chips not designed to be writable however a writable version is available and based on T5577 chip.
There’s a number written on those, 10 digits not sure what that is yet.
However, the frequencies commonly employed for LFID (Low-Frequency Identification) or LowFID systems are typically 125kHz and 134kHz. It’s important to note that these frequencies serve as the foundation for low-frequency RFID technology. In and of themselves, these frequencies do not possess inherent functionality for activities such as ID identification, reading, or writing.
Commonly utilized low-frequency cards encompass brands like HID, T55xx, EM410x, and other similar series. These types of low-frequency cards are frequently encountered and used in everyday life by many individuals.
Not being able to read the tag with my phone suggests that it’s not a Mifare chip, I can’t go anywhere without being able to read it, shopping time !
here’s what I got :
Hypothesis 01 :
before diving into any code, clone a tag using the cheap handheld 125Khz RFID Writer, if it works means they’re 125Khz, try writing to my current tag, if it’s possible means they are T5577 othrrwise they’re 4100 family
Hypothesis 02:
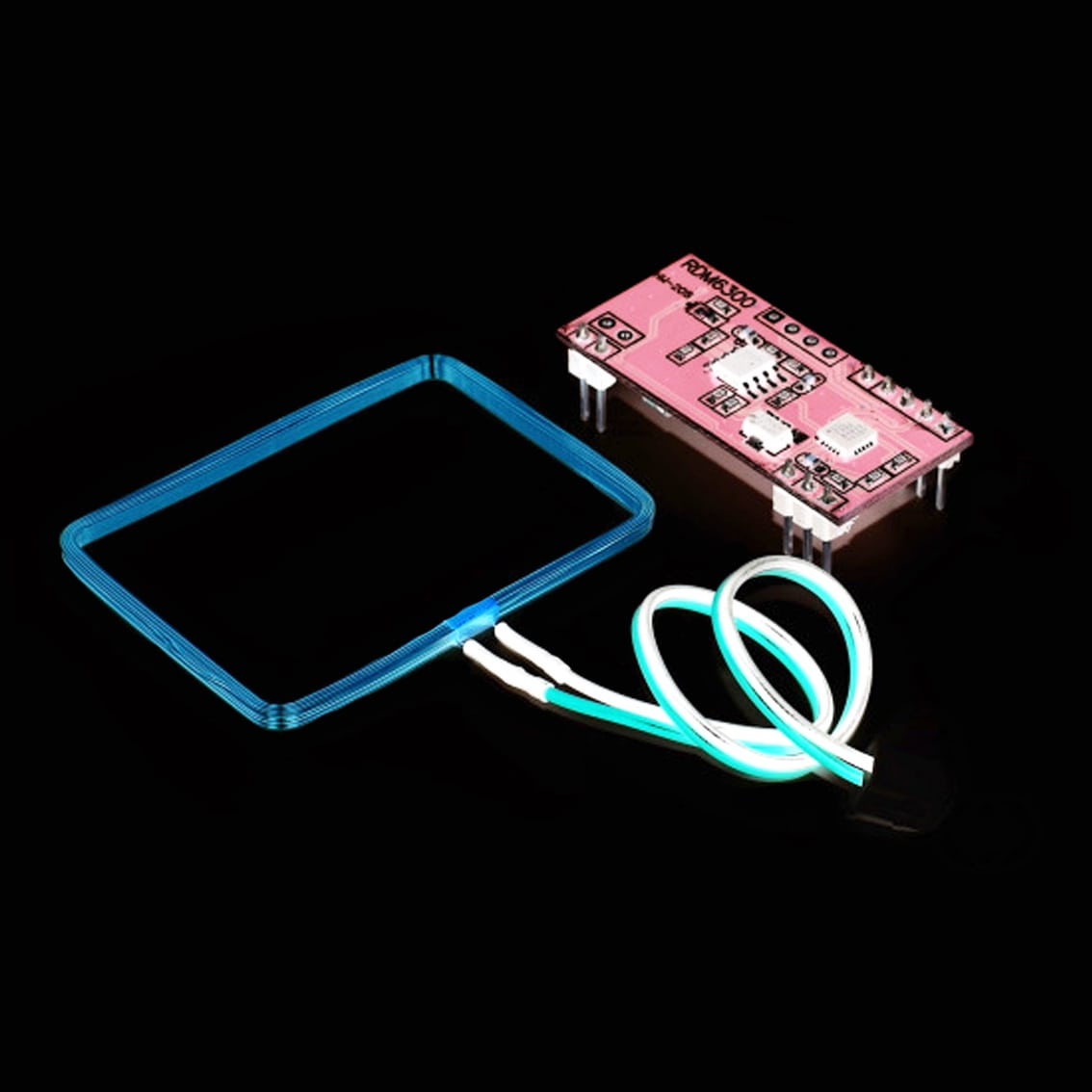
Build a reader using the RDM6300 and see what kind of informations we get from reading
Experiments :
observations
By cross-referencing the EM4100 datasheet and the RDM6300 example code we can tell :
- tags are 64-bit data
- 9 bits in the header (probably a reading trigger)
- D00-D93 body construction (data)
- PR0-PR9 parity check per row
- PC0-PC3 parity check per column
- E0 closing bit
| Header | 1 1 1 1 1 1 1 1 1 | ||||
| Message | D00 | D01 | D02 | D03 | PR0 |
| D10 | D11 | D12 | D13 | PR1 | |
| D20 | D21 | D22 | D23 | PR2 | |
| D30 | D31 | D32 | D33 | PR3 | |
| D40 | D41 | D42 | D43 | PR4 | |
| D50 | D51 | D52 | D53 | PR5 | |
| D60 | D61 | D62 | D63 | PR6 | |
| D70 | D71 | D72 | D73 | PR7 | |
| D80 | D81 | D82 | D83 | PR8 | |
| D90 | D91 | D92 | D93 | PR9 | |
| PC0 | PC1 | PC2 | PC3 | E0 | |
Let me break this out a little bit more with an example, let’s do the reverse math for the tag I used to test on the RDM6300
the number on the tag is : 0009622573
RDM6300 is returning :
Message-Data (HEX):
49 (version) 0092D42D (tag)
Extracted Tag: 9622573
0092D42D is basically the decimal to hex conversion for (000)9622573
but that 49 marked (version) is really intriguing and doesn’t correspond to anything visible on the tag
from the comment on line 2 in the example code let’s assume this should build this way :
(header)+ [(version)+(tag)+(tail)]
let’s do a binary table and check if this works
| Header | ||||||
| Hex Tag | Binary | Message | RP | |||
| 4 | 0100 | 0 | 1 | 0 | 0 | 1 |
| 9 | 1001 | 1 | 0 | 0 | 1 | 0 |
| 0 | 0000 | 0 | 0 | 0 | 0 | 0 |
| 0 | 0000 | 0 | 0 | 0 | 0 | 0 |
| 9 | 1001 | 1 | 0 | 0 | 1 | 0 |
| 2 | 0010 | 0 | 0 | 1 | 0 | 1 |
| D | 1101 | 1 | 1 | 0 | 1 | 1 |
| 4 | 0100 | 0 | 1 | 0 | 0 | 1 |
| 2 | 0010 | 0 | 0 | 1 | 0 | 1 |
| D | 1101 | 1 | 1 | 0 | 1 | 1 |
| CP | 0 | 0 | 0 | 0 | 0 | |
the complicated math :
header (9 bits) + message (40 bits) + row parity (10 bits) + column parity (4 bits) + closing (1 bits) = 64 bits
that’s poetically matches to the entire memory stamp of an EM4100
conclusions
- Version number cannot be retrieved by visual recognition on the tags
- Conversion from the number on the tag to the reader seems go this way :
Serial Number (décimal) → Hexadecimal → Binary
- This conversion gives us the software path to emulate a tag, but also that there’s a minimum and maximum value to a tag, which means a bruteforce is practicable, in fact, since the key conversion is a 10 digits hex number [version]+[tag] means :
- the minimum value is [00][00000000]
- the maximum value is [FF][FFFFFFFF]
practice
let’s put this to practice, we can clone these tags with the handheld 125Khz cloner from EM4100 to T5577 tags that are writable, but that is restrictive and too bluky to be effectively used stealthy in the field
I need to make a gadget/tool for this kind of access controller, it’s already covered by the flipper zero and the proxmark but both suffers from a high price, lack of availability and flagged, I need something I can shape stealth and open source to the community
Features to embed :
Emulate any tag
Read tags and get Version & Tag hex values
Save read values in a slot system
Select a slot from the memory and replay the values
Bruteforce
Enter Tag values manually and bruteforce the version number
Write to T5577 magic tags
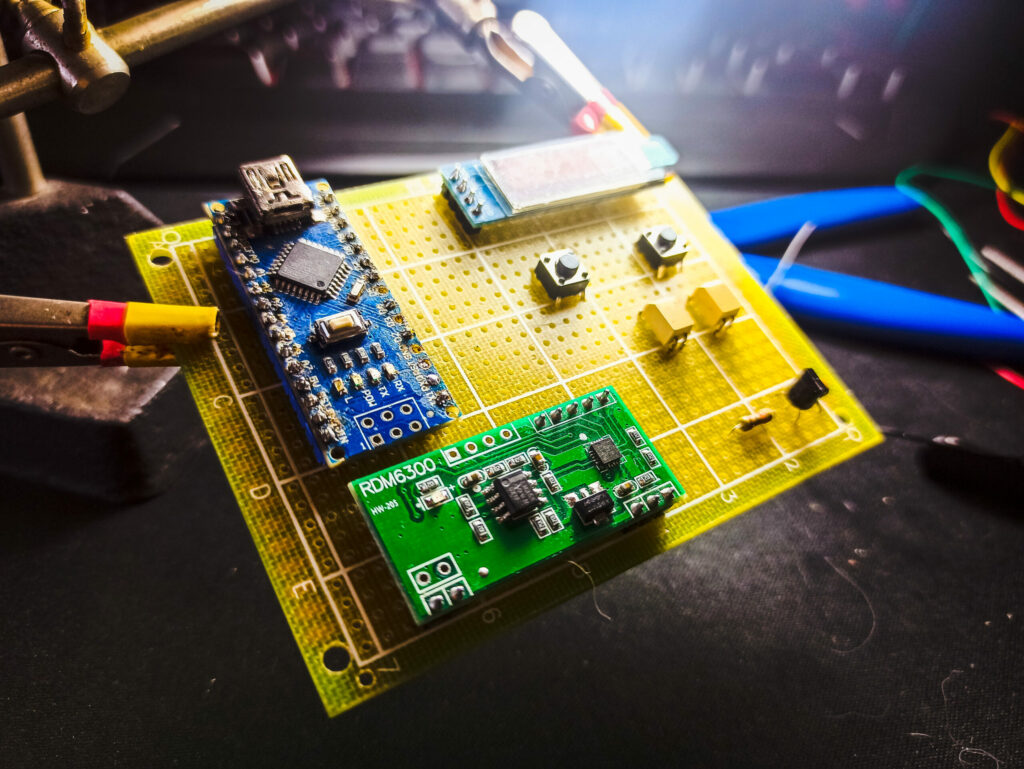
The reading part is perfectly done via the RDM6300 so I am just going to rely on it and build a device around it, I am going with Arduino Micro spared from an old project and a 0.91″ i²c oled screen
Let’s work on the key feature, Emulating
emulating
Even if marketed as read/write module the RDM6300 is only able to read, or at least I’ve never been able to to use it for writing.
If I want to emulate a tag I will need extra electronics for that, since I suspect the antenna to be a simple inductor tuned and detuned by the EM4100 chip doing only high/low states at the right frequency, I built a simple resonating circuit that will be controlled by the µC
normally the circuit should be tuned by the resonance formula but since that I am gonna reuse the RDM6300 antenna, I winged standard values to the components, the antenna is something around ~860uH
extra note for the software part is that the data seems to be modulating the signal through a manchester encoding, also from the datasheet ~
And this worked incredibly well, event tried it on the reader and I’ve been gracefully granted access with a green light
Now this means we can read and emulate tags, the tag values can be retrieved from the RDM6300 we only need to convert it to 64bits binary and do the parity check
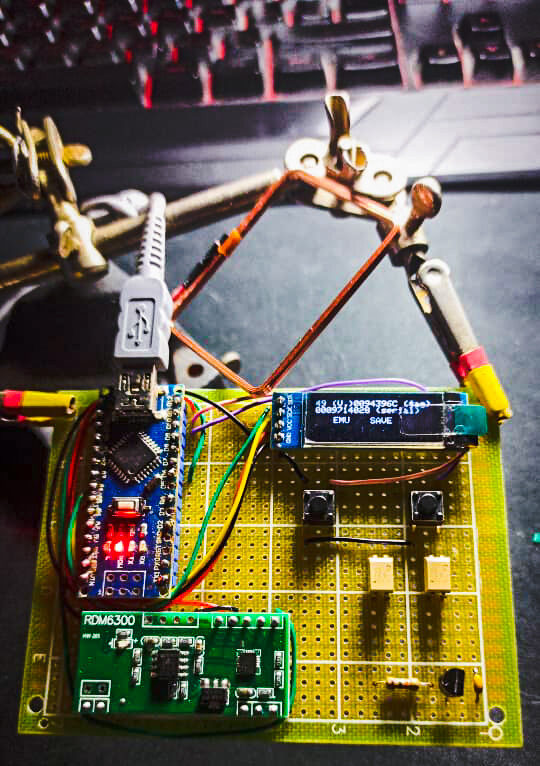
putting all this together and the NFCat will see the light
NFCat
Hardware Notes :
Using the same antenna for the RDM6300 in reading and the tag emulator was not possible, the signal line was noisy because each one was tuning the other, solved it by air-gapping the lines with optocouplers, PC817 from my shelves, transistors would’ve made the trick but I choosed the safety.
Designing a menu navigation was a pain, I am really bad with front-end coding but made my best for a minimal buttons configuration with only two buttons, well three buttons if we count the arduino reset button I used go back to the main menu, it’s resetting the AT328P and taking to the main menu 😂 ✅
2 buttons, 4 functionalities :
Short press left/right → navigation
Long press left → back, cancel
Long press right → enter, validate
Main menu :
Read :
Save
Emulate
Emulate
Emulate
Credit


Bravo